At Caudena, our blockchain intelligence team has been hard at work understanding the patterns of cryptocurrency mixing service “eXch” (exch.cx), including its connections to the Thorchain ecosystem. While eXch would perhaps dispute using the terminology ‘mixer’ to describe their cross-chain swap service, Caudena’s on-chain analysis shows that a significant percentage of users are using it solely for obfuscation purposes – by swapping funds to another chain and immediately swapping back to the originating chain.
This analysis comes in light of eXch’s recent confrontational stance, as they defend their active facilitation of laundering proceeds from the recent $1.5 billion ByBit hack.
Refusal to Cooperate
eXch has publicly refused to cooperate with ByBit following the $1.5 billion hack conducted by North Korea’s Lazarus Group despite evidence showing that a portion of these stolen funds are actively being laundered through eXch’s service. Rather than assist in recovery efforts, eXch posted screenshots on Bitcointalk revealing their refusal to cooperate, citing “reputation harm” from ByBit due to their addresses being labeled as “high risk”.
While they claim that “the insignificant portion of funds from the ByBit hack” that entered their service was “an isolated case,” our analysis indicates ongoing laundering activity. Their claim that they are “NOT laundering money for Lazarus/DPRK” is contradicted by conclusive blockchain evidence showing their continued processing of funds related to the hack.
Regulatory Defiance and Antagonism
Last month, eXch had published an adversarial “demand letter” on Bitcointalk, directly challenging major regulatory bodies including the IRS, DOJ, SEC, and OFAC. The service explicitly threatened to implement additional obfuscation measures if their demands weren’t met, demonstrating a clear intent to evade regulatory oversight.
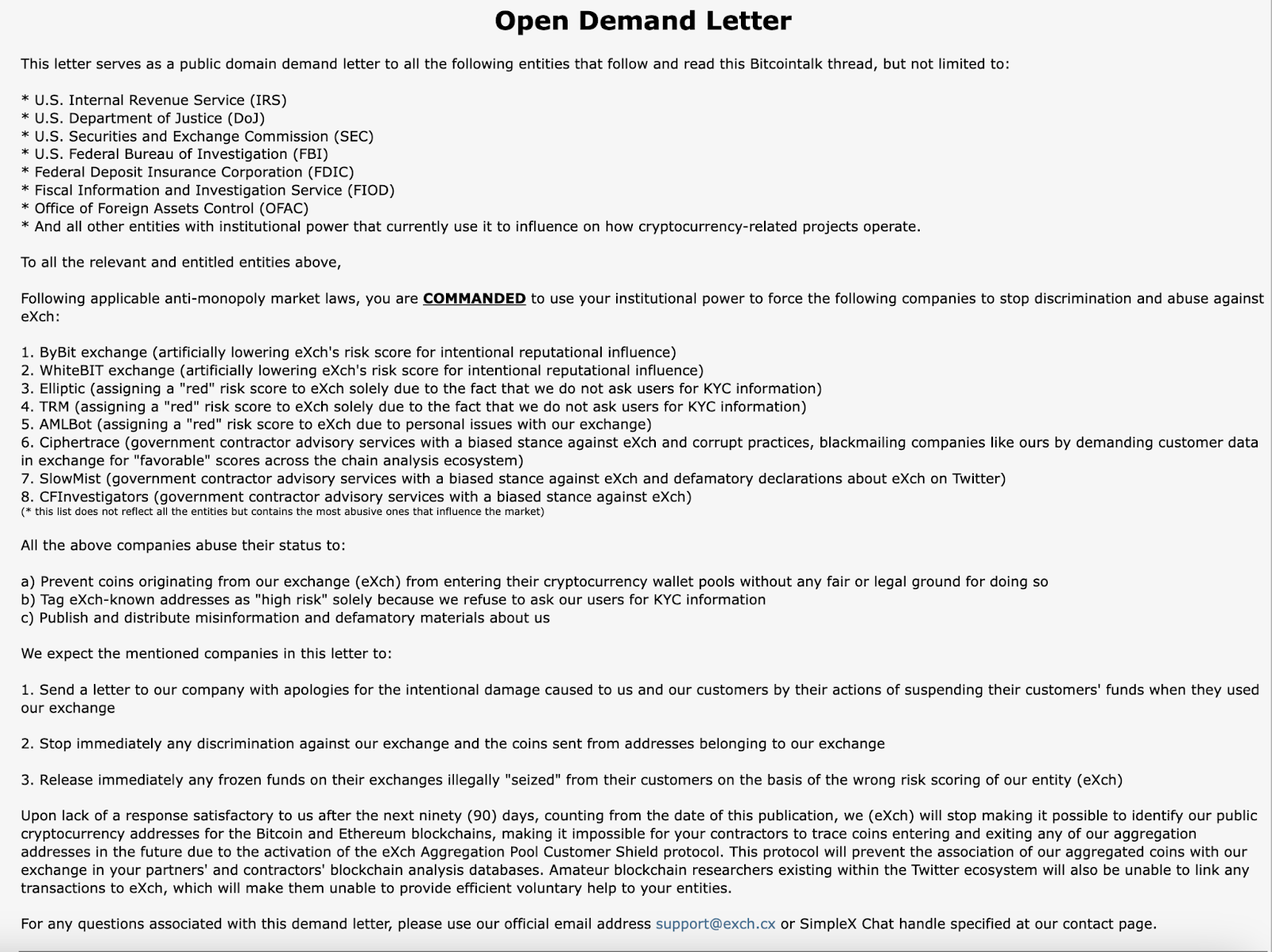
The “Demand Letter”
The letter asks public agencies and private companies to “stop discrimination and abuse” towards eXch, claiming that analytics tools are targeting them by labelling them as high risk.
They have previously mentioned that they have not responded to any disclosure request from law enforcement agencies, as they “considered all their requests illicit”.
eXch has now also launched an aggressive campaign against blockchain researchers who have documented their role in money laundering. In a February 22nd post, they attacked researcher ZachXBT, calling him “toxic, incompetent, and generally untrustworthy” after he identified suspicious transactions.
Despite their claims that on-chain researchers are conducting a “targeted FUD attack,” blockchain evidence Caudena has collected confirms eXch’s ongoing role in processing ByBit hack proceeds.
On-Chain Analysis
Our on-chain analysis of eXch activity has shown $2.3 billion in total funds processed across:
- Bitcoin: $932M, ~45K addresses

- Litecoin: $276M, ~105K addresses

- Ethereum: $1.18B, ~82K addresses

Notably, 30-40% of incoming funds originate from mixer (eXch), with 25-35% of outgoing funds directed back to mixer (eXch) – a pattern consistent with deliberate obfuscation rather than legitimate swap activity.
At Caudena, we use our industry-leading fingerprinting tools alongside other heuristic approaches to cluster addresses linked to target entities. Our analysis of unique changes in on-chain patterns has led to us having what we believe to be the most comprehensive eXch transaction data on the market.
Despite eXch claiming that they “do not aggregate UTXO’s on single addresses for other coins [other than ETH], making traceability of our exchanges nearly impossible for chain analysis platforms”, we believe that we have identified the vast majority of eXch transactions on all chains except Monero and Dash.
On the Bitcoin blockchain, we identified distinctive sweep transaction patterns which we were able to link to eXch and identify a large number of funds attributed to eXch swaps.
We have developed a pioneering capability to track cross-chain transactions, allowing us to follow funds as they move between different blockchains through services like eXch.
Our pioneering cross-chain tracking allows us to follow funds as they move between different blockchains; for eXch, we have gathered comprehensive cross-chain swap data on 45% of high-value Bitcoin transactions, 38% of Litecoin transactions, and 22% of Ethereum transactions.
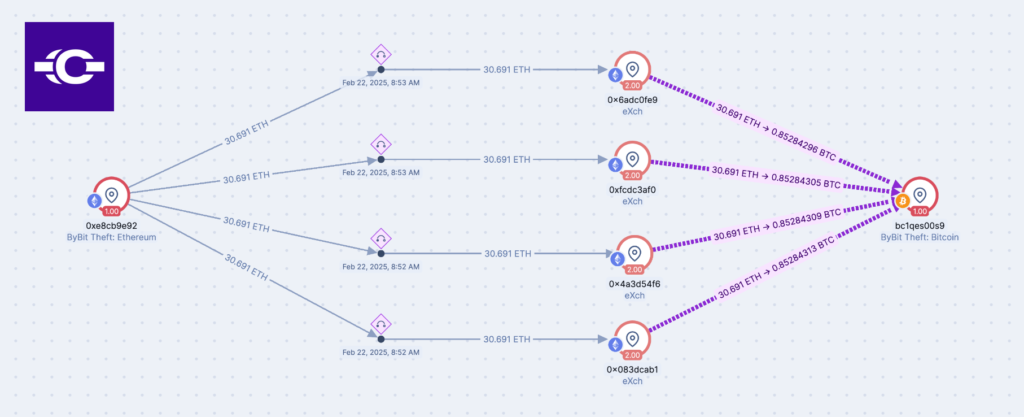
Analysis of the cross-chain data conclusively shows that eXch operates primarily as a mixing service rather than a legitimate swap provider, with users converting funds from one blockchain to another only to convert them back – a pattern consistent with mixing rather than legitimate swap activity.
THORChain Integration
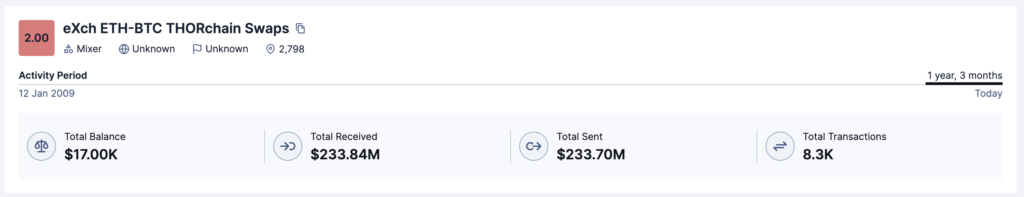
Our tool shows eXch is heavily dependent on Thorchain for swapping liquidity.
8% of inflows and 17% of outflows from the Bitcoin cluster, 49% of inflows to the Litecoin cluster, and 20% of inflows to the Ethereum cluster were facilitated by Thorchain.

eXch believe the “witch hunting” they have received is disproportionate, and that “for some reason, [Etherscan] haven’t put such warnings for Thorchain Ethereum addresses, that have already processed more than 200 times the total amount we processed yesterday and will continue.”
eXch also offers an option to swap ETH to BTC directly via Thorchain – an option which, our analysis shows, is almost exclusively used by illicit actors.

The eXch frontend instructions for Thorchain-enabled ETH-BTC swaps
Caudena has identified and clustered these eXch swaps facilitated via Thorchain, of which over $160 million are linked to the ByBit theft funds from the previous two days (25th – 27th February).
Conclusion
Given eXch’s recent aggressive public stance against law enforcement, explicit rejection of any anti-financial crime measures or cooperation with hack victims, combined with our on-chain analysis, we reiterate our evaluation of eXch as a significant risk to the crypto ecosystem.
We are seeing precedent where both centralized and decentralized privacy tools are implementing controls against processing illicit funds, often on-chain – Railgun’s on-chain privacy pools protocol is a great example; Chainflip implemented a protocol-level upgrade to block illicit swaps in response to the ByBit hack; even Wasabi Wallet (zkSNACKS) integrated compliance checks in their coordinator before eventually shutting down. We strongly believe that it is possible to engage with decentralized protocols and services to implement controls that deter bad actors, without impacting regular users’ privacy.
There is no room in our industry for bad actors such as eXch that undermine the integrity of the crypto ecosystem and knowingly process transactions known to fund North Korea’s regime.
We continue to monitor the situation and assist law enforcement in demixing illicit funds, and taking down bad actors in our industry. We continue to treat any funds originating from the service as high risk mixing activity.
For more information on our solutions, book a demo with us.
